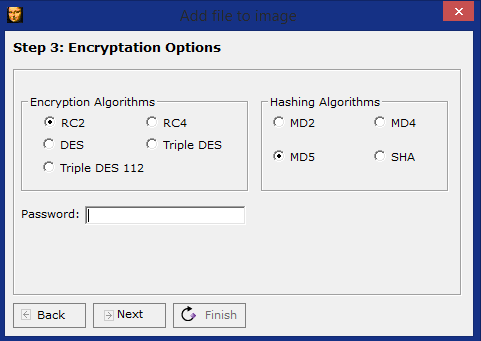
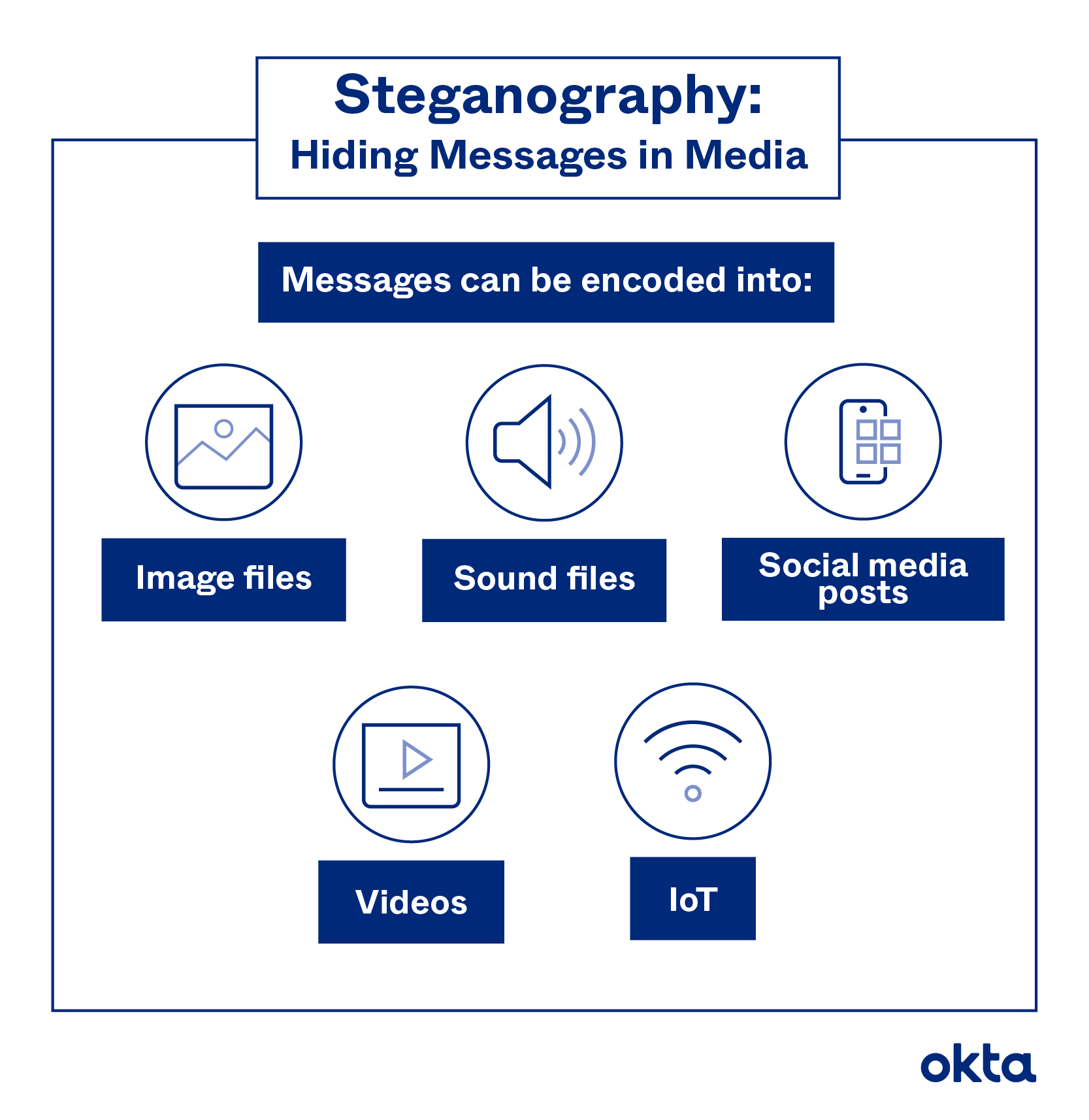
Steganography: How to Hide Secret Data Inside an Image or Audio File in Seconds « Null Byte :: WonderHowTo
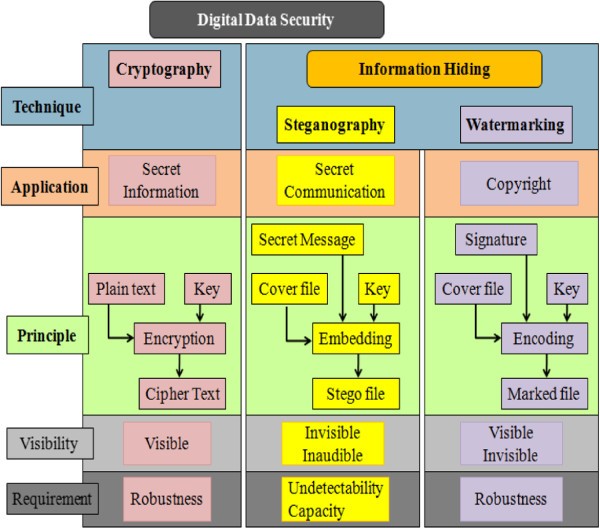
Comparative study of digital audio steganography techniques | EURASIP Journal on Audio, Speech, and Music Processing | Full Text

Steganography Tutorial | Hide Secret Text Message Inside Image Using Python | GUI Tkinter Project - YouTube

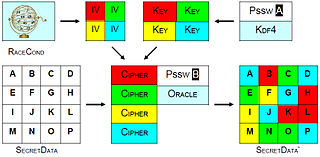
Business process flow and the interaction among data hiding tools and... | Download Scientific Diagram

An improved location mapping and cover synthesis based data hiding by model SSSP problem generation | SpringerLink
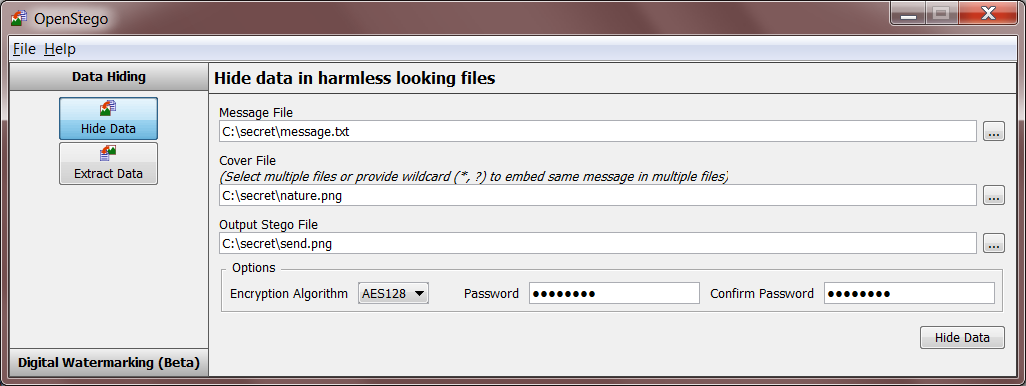
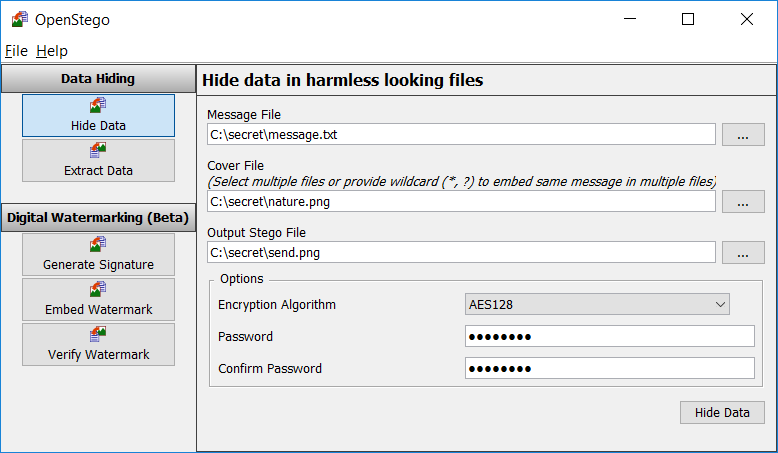
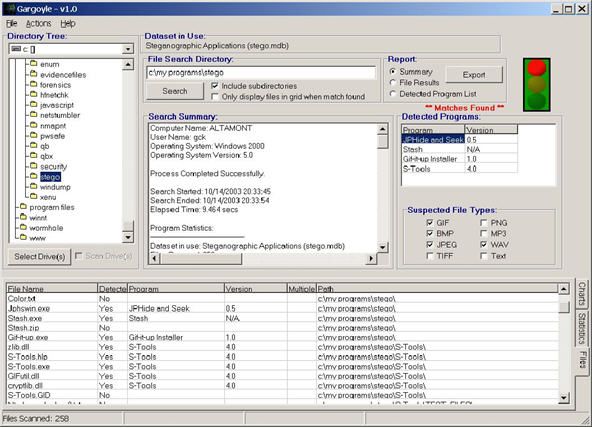
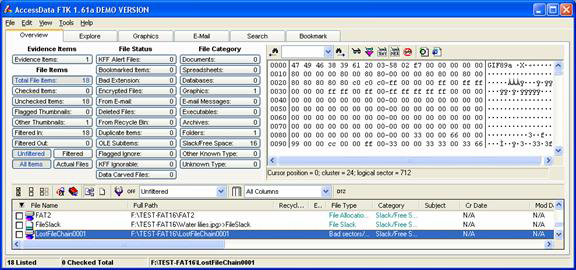
OpenStego - A Tool For Data Hiding And Digital Watermarking - Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses